According to a survey , the forecast of global expenses by companies, coming from cyber crimes, will continue to increase and should exceed $ 6 trillion annually by 2021 (nearly $ 33 trillion in the current dollar price).
If you do not want your business to be part of this statistics, it is essential to invest in cyber security.
Cybercriminals are always looking for new ways to overcome or divert security software and gain access to networks and devices with personal and business data, with new attacks as well as changes in “usual” attacks.
For you to get an idea of the dimension of the problem, Mundo Mais Tech released the 10 cyber threats in the first half of 2020 , identifying that attacks only using remote access in Brazil, grew 330%.
Testing your network can highlight where threats may come from and show the actions you need to increase your protection. Grouping this data, you can create an overview of which weaknesses are small and which are major problems that need high priority investigation.
But are there reliable vulnerability tests of the internet? Yes!
We'll see more about it in the next lines.
Vulnerability tests

As the name implies, Internet security tests assess the possible vulnerability points related to blocking or release of sites considered harmful, or improper, dangerous, and outside work.
There are some distinct forms of internet security tests. The door test, for example, checks for any safety breach at the server or router ports. DNS query based, checks if it is possible to access websites framed in the harmful categories and inappropriate content and then shows which categories are released and which are blocked by some software or lock system.
By combining the information, you can have a good idea of the state of your cyber security configuration and protect yourself better.
To assist companies, we have listed 3 internet security tests and their features, which you can see below.
SHIELD TEST
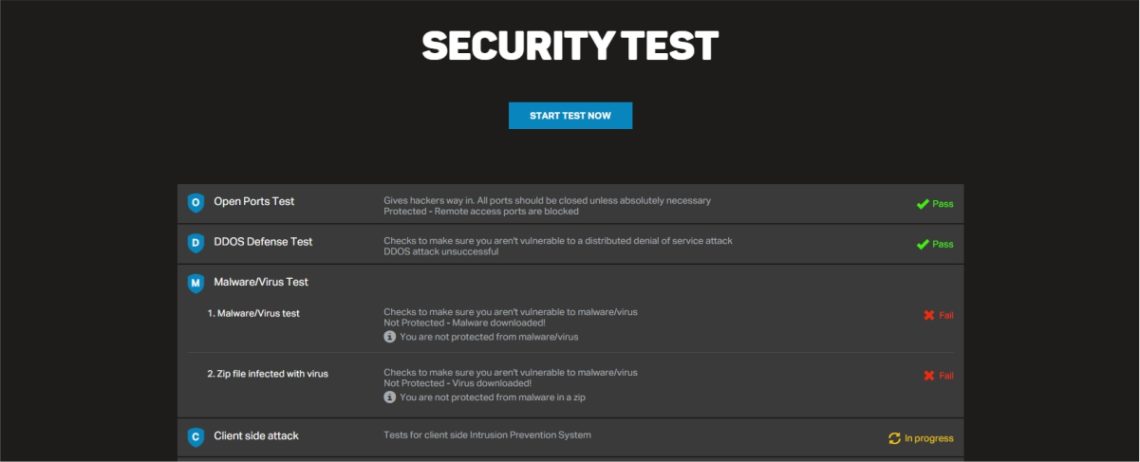
SHIELD TEST measures the susceptibility of your network to the infection and evaluates existing levels of defense against potential attacks.
The test sends malware samples transmitted by the tool server and performs a self -assessment. But rest assured! Once the test is completed the data is removed. Therefore, while this test uses real malware samples to ensure it is legitimate, there is no risk of infecting your system.
Vulnerability test analyzes the following items:
- Open doors test
- Defense Test DDOS
- Malware / virus test
- Data theft test
Door Test
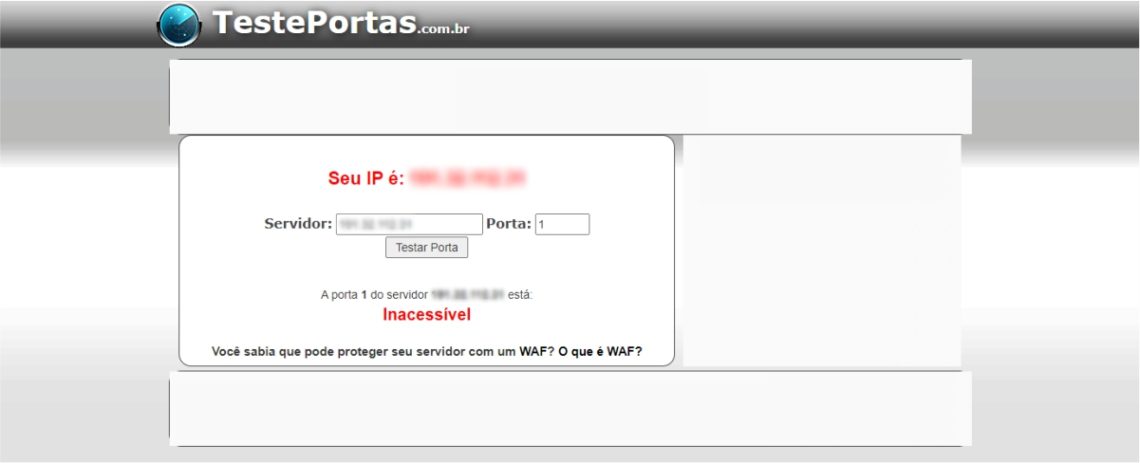
When it comes to ports of a server or router, it is usually referring to the TCP and UDP doors, which are protocols used by software and services of the network communication operating system and, consequently, on the internet.
Systems connect in these ports and start communication with the server. But for this the desired door needs to be open, otherwise the system will not be able to connect, resulting in error.
On the other hand, keeping open doors you do not use can mean unnecessary exposure, increasing the risk that these doors are exploited by hackers in search of system vulnerabilities, allowing the invasion of services.
In this sense, testing the router is also important, because if your router has an open door, it can also be used for attacks. Make sure your router management interface, which usually uses the 80 (http), 443 (https) or 22 (SSH) ports, is protected and is not exposed on the internet.
The doors test makes the door test that is possibly prone to attacks and identifies as inaccessible or accessible.
Be sure to test whether your network has exposed any remote desktop server, or Remote Desktop, which works at the TCP 3389 . Currently it is recommended not to keep the Internet Desktop Remote Desktop service due to the high risk of ransomware attack. Even the FBI has already issued alert about the risks of exposure of the remote Windows work area on the internet. To protect the remote desktop, it is recommended to use a business VPN service.
Lumiun Security Test
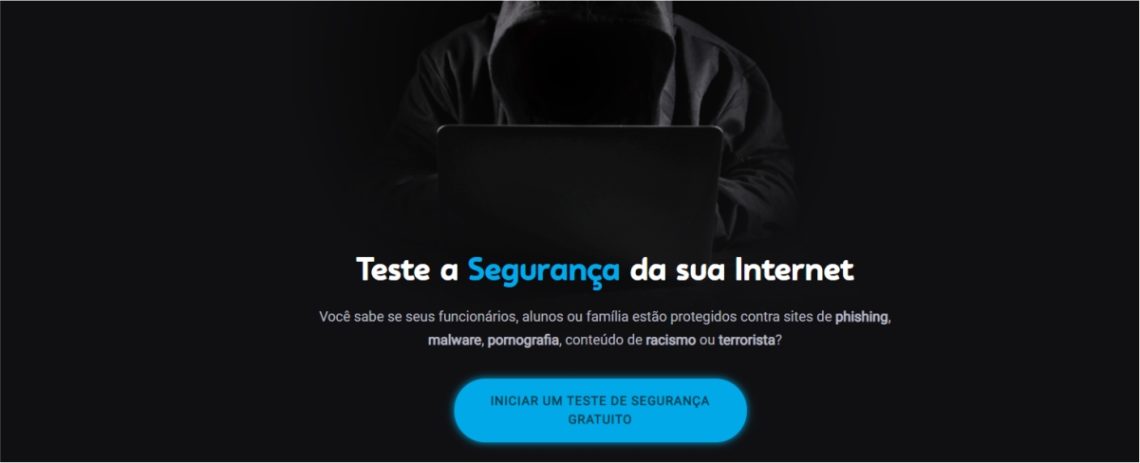
Do you know if your staff, students or family are protected against phishing sites, malware, pornography, racism or terrorist content? The Lumiun Internet security test shows you.
Unlike those mentioned above, the Lumiun test is based on DNS layer requests, ie identifies which categories of websites are released or not for access from your network.
To be more accurate, you will be made access requests to various sites that are within the categories considered insecure, from your internet connection.
See some of the categories:
- Phishing and online fraud
- Malware and Spyware
- Access Anonymitors
- Drugs and alcoholic beverages
- Games and bets
- Pornography and nudity
- Violence, terrorism and racism
Result s

Well, seeing some vulnerability tests and their results, it's time to draw a cyber security plan. If you have a IT professional in your business, it is interesting together with it, identifying the best way, or tool, to improve data security in the company.
Business security tests are essential for helping to protect important data and information against cyber attacks.
Here are some cases of major security failures in article 10 largest data security failures in 2020 on our blog.
We hope that, by ending this article, reading will help you and your business to stay safer on the internet.
To the next!













3 Comments
Comments closed