It has been a long time since phishing attacks have been a constant concern between users and companies on the internet. For this reason, some tools have been developed and enhanced in order to ensure greater protection of data from people and corporate internet users.
Basically, a phishing attack involves three essential factors:
- Choice of the type of communication: which can be email, telephone, SMS services, copies of legitimate websites, false advertising, among others;
- Disguise : Cybercriminable seeks to pass for an institution, company or confidence contact of the victim;
- Strike : Through social engineering, he can fool the victim and obtain confidential data such as documents, credit card numbers and other information.
Thus, we can see that, regardless of the medium used, the purpose of the phishing blow is basically the same: obtaining data fraudulently in order to favor other types of coup , such as financial fraud and credit card cloning.
The growth of social networks allowed criminals to gather even more information about their victims. Through these platforms, they can know the full name, birthday, family, frequent contacts, places where the victim frequents, a company where she works and much more.
The dangers of social engineering
Social Engineering is a set of practices and techniques used to deceive and persuade a victim . With the help of this tool, cybercriminals can obtain access data or confidential information more easily using human vulnerability to it.
A social engineer is a figure that has very ease of communication, aptitude for persuasion and self -confidence. Advantages that can be used to obtain information and favor traps.
This feature is critical for a phishing blow to succeed. This is because the more realistic or persuasive the content of a fake email , for example, but it will be easy to get the victim to access a malicious link or download a file to your computer. But how does this work in practice? Watch this video and better understand how social engineering can be used: social engineering, the art of mistake!
Hackers who specialize in social engineering can use human emotions such as curiosity, fear and insecurity to manipulate their victims and achieve their goals.
Unlike what you think, social engineering is not a resource used only for phishing blows. There are other attacks that can be favored with this strategy , as we will see below.
Baiting
In this type of scam, the hacker uses a false promise to arouse the user's interest or curiosity. This way, he can collect his data effortlessly and favor other types of scams.
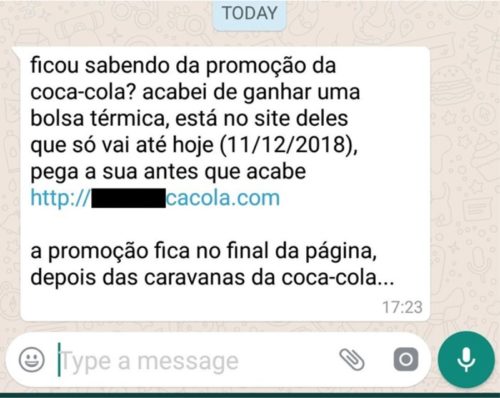
Quid pro quo
In this case, the attacks are based on excessive confidence , that is: there is a certain exchange of information so that the apparent relationship is fair to the user. This type of scam is common to be applied to users who need technical support, for example.
The trap causes it to provide login information, but ends up delivering control of your computer to the cybercriminals.
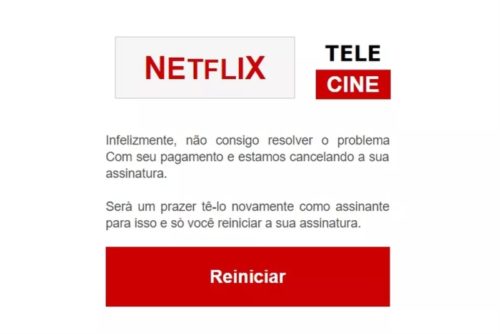
Vishing
Vishing is similar to phishing attack, but instead of using fake emails or websites, hacker uses telephone calls to deceive your victim and collect confidential information.
Scareware
This type of scam is very common and you have probably been through this. The victim receives messages from SOS, alarms and threat notifications, which are created to make the user think that he is experiencing a cyber attack or that he is infected with a virus or malware.
That way, it ends up installing software to solve the problem, but this file is the real trap. See some examples below:
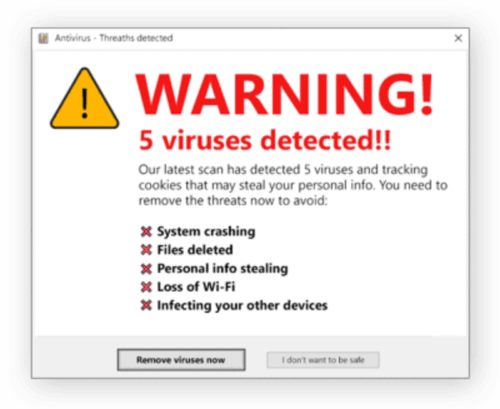
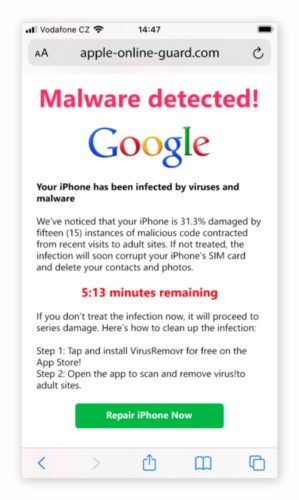
How can this trap harm your business?
It is common to think of phishing as a threat to users individually, but it is important to remember that within a company, using work hours and the organization's computers, employees can also be victims of coup.
When the victim does not realize that she is facing a trap or fraud, she can provide personal data, confidential information from the company or favor financial blows. For example, through the phishing blow , the hacker can access the company's computers and apply a scam known as ransomware .
Through this scam, it can steal information, corrupt data and unavailable systems totally, impairing the profitability of the business. From then on it can request a redemption to return this information or restore company systems. All of this, in addition to generating the unavailability of the services provided by the business , also causes major financial losses.
Among the main consequences of phishing for the company, we can mention:
- Computer contamination by malware that can damage data and corrupt networks ;
- Turn company computers into bots (zombies computers used in DDOS type attacks );
- Spam shot;
- Damage to the company's image in the market and the relationship with customers;
- Invasion of accounts;
- Access to cloud services ;
- Financial blows;
- And many others.
What are the best phishing protection tools?
1. Safe use policy of the internet
Before thinking about a phishing tool or feature that helps protect themselves, the company needs to have an internet use policy that ensures users know how to deal with and avoid threats in the online environment.
This policy helps to make your employees aware of the use of the internet and the good practices that should be applied during your day. The present time we are, with Black Friday , this awareness becomes even more important. Cybercriminals use this date to plant increasingly efficient traps and collect information fraudulently .
2. Business Firewall
There are today several software and tools aimed at protecting against cyber threats. These systems block dangerous content on the corporate internet, helping to reduce the incidence of fraud and blows from this channel.
3. Antivirus and Antimalware
These tools help block malicious files that arrive from various channels, such as emails, malicious pages, among others. Relying on these features can help block dangerous files that can be sent via phishing emails.
4. Password Manager
The password manager is an encrypted database that helps store a large amount of password safely and practical. To facilitate the process, the user uses a single password, avoiding the need for redefinition of passwords, a trap widely used by cybercriminals.
5. Employee Training
One of the most efficient ways to protect your company from threats from phishing blows is through an employee training process. It is essential that everyone involved understand the importance of using the company's internet with intelligence and wisdom.
Safety problems created by phishing blows come from the ingenuity or unpreparedness of users, so that training gains a prominent role in combating this dangerous threat.
6. Website lock tool
In addition to the internet use policy, the company can use a website blocking website to ensure that major threats do not reach its employees.
Through it, it is possible to manage content access patterns that pose some risk to information security within the company , such as entertainment site, e-commerce, social networks and personal emails.
Meet Lumiun Box
Lumiun Lumiun Box is a small and medium -sized tool that controls internet access, blocking websites and connections and avoiding phishing . With the help of Lumiun Box , it is possible to avoid attacks on the company's network and also improve team productivity by managing access considered harmful and outside the scope of work .
With an intuitive and easy -to -use tool, the company can ensure consolidated information about the use of the internet at work.
In addition to access management, Lumiun Box delivers reports with the most accessed sites, times, categories, users and more. It can also help to create an Internet access policy with personalized rules based on the collected data.
Want to know more about this tool against phishing? Click here and find out everything she can do for you!









