The invisible conductor behind the connections
IT professionals often observe the "magic" that happens behind the scenes when a user types an address like Lumiun.com in a browser and, in seconds, the page loads. Behind this apparent simplicity, there is a robust and key system for the internet as we know it: the DNS, or domain name system . For the IT community, understanding DNS is not just a technical curiosity, but a key point to ensure the safety and efficiency of networks under its responsibility.
In this article, we propose a detailed analysis of the DNS. We will address its origin, understand its operation clearly and with analogies that facilitate understanding, explore its benefits and, very importantly, the associated risks, especially in the context of information security. The goal is that at the end of reading, the IT professional has a solid understanding of how this system governs the Internet traffic and how it can be used to protect corporate networks.
Prefer to watch? We prepared a complete video on the theme:
Once upon a time, before the DNS: the internet in the early days
Imagine a digital world where, to visit your favorite site, you need to memorize a complex sequence of numbers, something like 172.217.160.142 instead of simply Google.com . It looks like a nightmare, doesn't it? Well, this was the reality in the early days of the internet, before the emergence of our hero, the DNS .
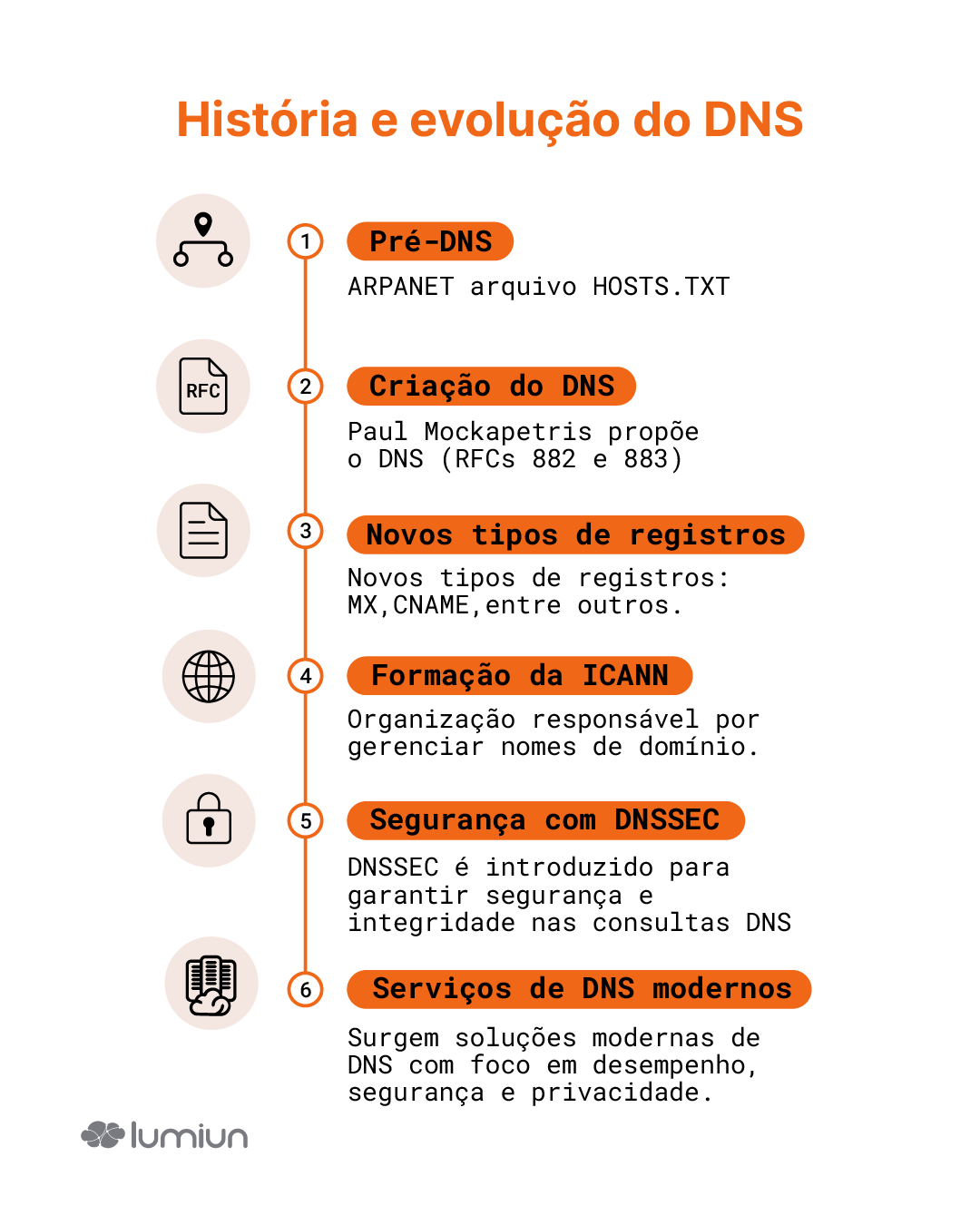
ARPANET CHALLENGE AND THE HOSTS.TXT FILE
In the 1970s, Arpanet, the forerunner of the internet we know, was a relatively small community, with a few hundred computers (called hosts ). For these machines to meet, there was a central file called hosts.txt . Think of it as a manual and unique telephone agenda for the entire network. This file contained the name and numerical address (the IP address) of each computer connected.
The maintenance of this file was a complex task, centered on the Network Information Center (NIC), located at Stanford Research Institute (SRI). Network administrators sent updates (a new computer added, a change of address) and periodically compiled everything in a new version of hosts.txt. Each host on Arpanet then needed to download this updated list to know “who was who” on the network.
However, the success of ARPANET and subsequent adoption of TCP/IP protocols made the network “explode” in size. What was a viable solution for hundreds of hosts became a gigantic bottleneck. The problems were many:
- UNSUSTIBLE TRAFFIC AND LOAD: Host size.TXT grew exponentially with the number of hosts. Worse yet, traffic generated for each machine to drop the frequent updates overloaded the network and servers.
- Name Collision: How to ensure two different administrators do not choose the same name for their computers? The NIC even tried to manage unique numerical addresses, but had no authority over the names. A new host with duplicate name could simply “break” access to an existing host.
- Committed consistency: Keeping the hosts.txt file perfectly synchronized with the reality of a constantly changing network was an almost impossible mission. When the file was finally updated and distributed, some host could have changed address, or a new host added could have caused connection problems.
Ironically, Arpanet's own success made the hosts.txt obsolete system. The internet needed something smarter, more distributed and more scalable.
The need for a new solution
Arpanet pioneers knew they needed an alternative. The goal was to create a system that would solve the problems of hosts.txt, allowing the administration of the names to be decentralized. Each local administrator could manage the names of their own hosts and make this information available to the rest of the world without depending on a central entity for each small change. This would not only relieve the traffic and processing bottleneck, but also make updates much more agile. In addition, the new system should use a structure of hierarchical names, ensuring that each name was unique in the internet universe. The seed of the DNS was planted!
The birth of DNS: a silent revolution
The Hosts.TXT crisis catalized innovation. The Arpanet community needed an elegant and robust solution, and it came at the hands of a visionary.
Paul Mockapetris and the creation of Domain Name System
Responsible for architecting the solution that would forever change the way we sailed on the internet was Paul Mokapetris , from the University of Southern California Information Sciences Institute (ISI). In 1983, he published RFCs (Request for Comments) 882 and 883, which described the Domain Name System (DNS) . These documents were the precursors of specifications that would become the standard, RFCs 1034 and 1035, released in November 1987, which are still the basis of DNS we use.
The genius of Mockapetris's proposal lived in a hierarchical and distributed system. Instead of a central archive, there would be a network of servers, each responsible for a part of the "map" of the internet. The names would be organized in domains and subdominiums (such as Lumiun.com , where .com is the domain of top and Lumiun is a domain under it), ensuring uniqueness and allowing management to be delegated.
Evolution and Standardization
The introduction of DNS was not an isolated event, but the beginning of continuous evolution. One of the first and most important implementations of DNS server software was the Berkeley Internet Domain (BRIKEYY) , developed by students at the University of California, Berkeley, in 1984. Bind quickly became the most used DNS implementation on the Internet, a status it has maintained for many years.
Over time, DNS continued to evolve to meet the growing demands of the internet. Mechanisms such as:
- Notify: Allows a primary DNS server notify your secondary servers on updates, preventing them from having periodic consultations to check changes.
- IXFR (Incremental Zone Transfer): Allows only changes in a DNS zone to be transferred instead of the entire zone, optimizing updates.
- DNSSEC (Domain Name System Security Extensions): Adds a DNS security layer, helping to prevent certain types of attacks, such as cache poisoning (we'll talk more about it).
This ability to adapt and continuously improve is one of the reasons why DNS remains so vital, even decades after its creation.
How does DNS work in practice? Uncomplicating the magic!
Now that we know the story, let's get down to business for many IT professionals: how does this “magic” of name translation to numbers really happen? The good news is that, although it seems complex, the fundamental concept is quite intuitive, especially with the right analogies.
The analogy of the telephone list (or library catalog) of the internet
The most classic - and still very effective - analogy is to think about DNS as the telephone list of the internet . In the old days (some of us still remember!), To call someone, you were looking for the person's name on the list and found the corresponding phone number. DNS does something very similar: you type a domain name (eg lumiun.com ), which is easy for us humans to remember and use, and DNS translates it into an IP address (Ex: 192.0.2.42 ), which is the “phone number” that computers and servers use to find on the network.
Another useful analogy is that of a gigantic library catalog . You want a specific book (the site), but only know the title (the name of the domain). DNS is the cataloging system and librarians who, step by step, guide you from the correct section (top domain), the right bookcase until you find the exact book (the server with the IP address).
The main characters of DNS Resolution (the journey of an appointment)
For this translation to take place, a series of “characters” (specialized DNS servers) come into play. Let's know the main actors in this piece:
- The user and browser: It all starts with you, user by typing a domain name on your browser (or clicking on a link).
- RECISASE DNS RESOLVER (or DNS RECORDER): This is the first server your computer contacts. Generally, it is provided by your internet provider (ISP) or can be a public service, such as Google DNS (8.8.8.8) or Cloudflare DNS (1.1.1.1). Think of it as the helpful librarian who receives his request and is in charge of finding the information. An important feature of the resolver is the local cache : If he has already resolved that domain name recently, he can have the IP address stored and respond immediately, accelerating the process.
- ROOT SERVER AUTHORITATIVE SERVER: If the resolver does not have cache information, he asks a root server. There are only 13 "addresses" of root servers in the world (operated by various organizations and replicated globally). They do not know the final IP address, but know who is responsible for the top domains. It is like the great master index of the library , which points to the great sections. On the Root-Servers.org you can view a map where root servers are located.
- TLD Authoritative Server (Top-Level Domain): With the indication of the root server, the resolver asks the corresponding TLD server. TLD is the final part of the domain, such as
.com,.org,.Net, or country codes like.br,.pt. This server knows who is responsible for the domains within that specific TLD (eg who is responsible forLumiun.comwithin.com). It is the specific bookcase of our library. - Authoritative Name Server server: Finally, the resolver contacts the authoritative name server for the domain in question. This is the server that holds the official and definitive information about that specific domain, including your IP address. It is the final dictionary on the shelf , which contains the “definition” (the IP address) of the name you sought.
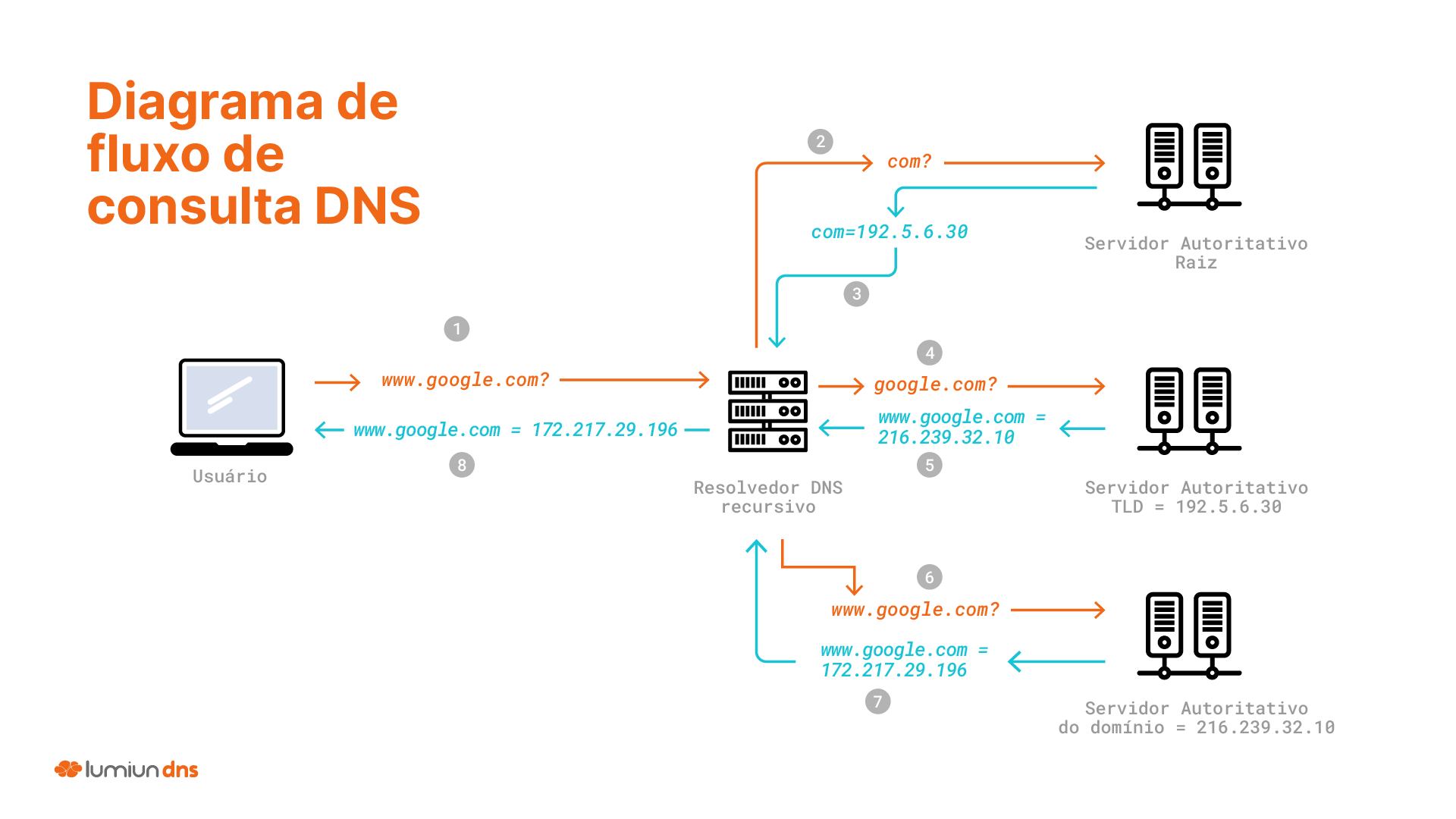
Step by step of a DNS query (without cache)
Let's view the full journey of a DNS query, assuming the information is not in any cache:
- You type
www.google.comin the browser. Your computer sends the query to the configured DNS resolver. - The resolver DNS recursive asks a root authoritative server: "Hey, who knows about
.com?" - The authoritative root server responds: “The TLD server to
.comknows. His address is192.5.6.30.” - The recursive resolver DNS asks the TLD server
.com: “Hello, who is responsible forGoogle.com?” - TLD Authoritative Server
.comresponds: “The authoritative name server forGoogle.comis216.239.32.10.” - The DNS resolver asks the authoritative name server from
Google.com: “What is the IP address towww.google.com?” - The authoritative name server responds: “The IP address is
172.217.29.196.” - The DNS resolver delivers this IP to your computer.
- Your browser now knows the “phone” of the site
www.google.comand can finally connect to it to load the page!
www.google.com recently, the answer can come directly from the cache, making it much faster and reducing the load on global DNS servers. It is system intelligence working to optimize the experience!DNS: Far beyond names and numbers - essential benefits
DNS is much more than a simple translator of names for IP addresses. It is one of the pillars that support the usability and robustness of the modern internet, offering a number of important benefits for both end users and system administrators.
- Ease of use of the internet: This is the most obvious and perhaps the most impactful for everyday life. Thanks to DNS, we don't have to be memorization geniuses to browse the web. Domain names like
Lumiun.com/blogare intuitive, easy to remember and share, making the online experience accessible to all. Without it, the internet would be a tangle of indecipherable numbers. - Scalability and Decentralization: DNS distributed and hierarchical nature is what allows the internet to grow exponentially without collapse. New domains and servers can be added continuously anywhere in the world, and the DNS system is in charge of propagating this information efficiently. There is no unique failure point that would bring down the entire internet (although attacks on root servers can cause large inconvenience, as we will see).
- Simplified flexibility and management: For those managing IT infrastructure, DNS offers immense flexibility. If you need to change the server that hosts your site to a new IP address, for example, simply update the corresponding DNS record. Users will continue to access by the same domain name, without even realizing the change behind the scenes. This simplifies migrations, maintenance and infrastructure updates.
- Possibility of additional and intelligent services: DNS is not limited to mapping a name to a single IP. It supports various types of records that enable a range of advanced services, such as:
- Load Balancing: The same domain name can be associated with multiple IP addresses of different servers. DNS can distribute requests between these servers, helping to avoid overloads and improving the performance and availability of web applications.
- Geolocation and Content Distribution Networks (CDNS): You can configure DNS to direct users to the geographically closer server. This is critical to CDNs, which store copies of websites in multiple local around the world to accelerate pages loading and reduce latency.
- MX E-mail Records: Mail Exchange (MX) records in DNS specify which servers are responsible for receiving emails to a particular domain, being a key point for the operation of e-mail.
- TXT Verification and Security Policies: Text Records (TXT) are used for various purposes, such as checking a domain ownership for Google Search Console, for example) and to implement Email Security Policies such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail) and Domain-Based (DMAINKEYs Message Authentication, Reporting & Conformance), which help fight spam and phishing .
In short, DNS is a silent but powerful gear that makes the internet more friendly, resilient and capable of supporting a myriad of complex services we use daily.
The dark side of DNS and the first line of defense of the network
Despite being a fundamental and ingenious component of the Internet, DNS, by its very nature and ubiquity, has also become a vector and strategic control in the scenario of cyber threats. Understanding the risks associated with DNS and, most importantly, how it can be used as a powerful first line of defense, is essential to protecting the networks and data that transit in them.
Why is DNS a critical point in security?
DNS is essentially the Internet's direction system. Almost every connection to an external feature (a website, an update server, a cloud service) starts with a DNS query. If an attacker can compromise or manipulate DNS answers, he can redirect users wherever he wants. However, this same DNS dependence to start connections makes it an ideal strangling point for safety: If an attempt to connect to a known malicious destination can be blocked even before DNS consultation is resolved for a dangerous IP , the threat can be neutralized at its early stage.
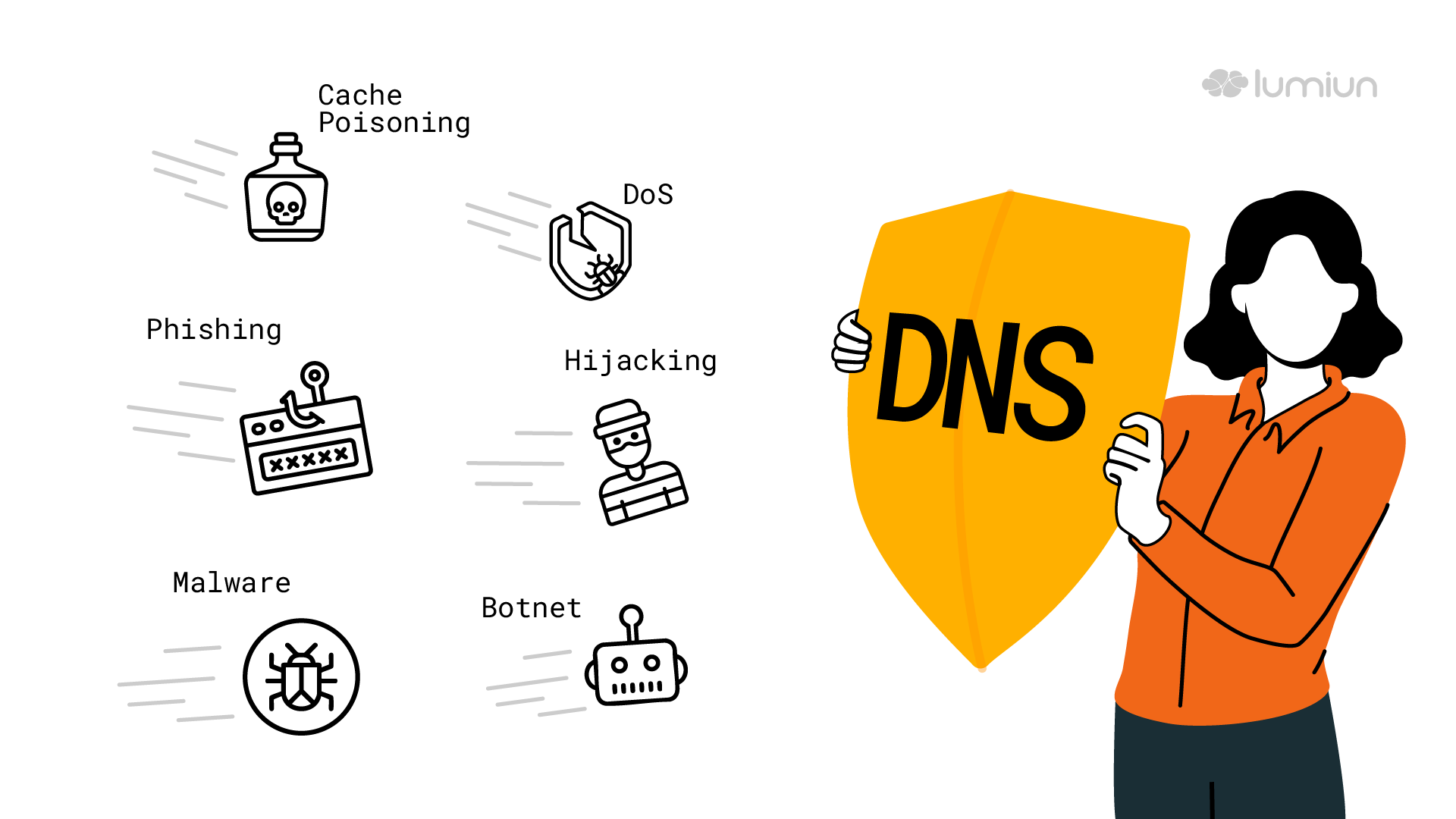
Threats that explore the DNS directly
There are threats that directly aim at infrastructure and the DNS protocol:
- DNS cache poisoning (DNS Cache Poisoning / DNS Spoofing ): An invader inserts fake information into the cache of a DNS server, causing it to provide a malicious IP instead of the legitimate. Users trying to access reliable websites are redirected for fake credential theft sites, bank data or malware installation.
- Denial Denial Attacks (DOS/ DDOS ) against DNS servers: unavailable DNS servers, preventing the translation of domain names into IPs and making sites and services inaccessible.
- DNS Hijacking: The criminal alters the user DNS settings, router or even domain register to divert traffic to malicious destinations.
- DNS amplification: A type of DDOS attack where invaders use open DNS servers to send massive answers to a victim, overloading their network.
- DNS Tunneling: The DNS protocol is used to encapsulate other types of traffic, creating secret channels for data exability or communication with control and control servers (C&C) malware.
DNS Filtering: A broad layer of protection against diverse threats
It is important to understand that the importance of DNS for security goes far beyond protecting against attacks that directly the DNS protocol. DNS filtering emerges as a proactive and highly effective security tool for blocking a wide range of threats that, although not “DNS attacks” in essence, depend on the resolution of domain names to achieve their goals. By controlling which domains can be resolved, companies can prevent users and systems from connecting to hazardous destinations on the Internet. This includes:
- Malware and Ransomware : Many types of malware and ransomware need to communicate with control and control servers (C&C) to receive instructions, send stolen data or obtain encryption keys. DNS filtering can block access to these known C&C domains, effectively neutralizing or hindering the action of malicious software.
- Phishing and fraudulent sites: Phishing sites are designed to deceive users and steal credentials or financial information. DNS filtering can prevent access to these known fraudulent sites, protecting users even if they click on a malicious link in an email or message.
- Botnets: Infected devices (bots) in a network communicate with a C&C server to form a botnet, which can be used for DDOS attacks, spam sending, etc. Blocking DNS server domains via DNS can dismantle or isolate these zombie networks.
- Newly registered domains (Newly Registered Domoins-NRDS): Many attacks use recently registered domains, as they have not yet been classified as malicious. Some DNS filtration solutions can identify and block or warn about access to these NRDs, which are statistically larger probability of being dangerous.
- Unwanted or unproductive content: In addition to safety, DNS filtering also allows companies to apply internet use policies by blocking access to categories of websites that can be inadequate to the work environment, such as social networks, games , adult content , unauthorized file sharing sites, etc., increasing productivity and reducing legal risks.
Protecting the Internet Gate: DNS SAFETY IN FOCUS
If DNS is the gateway to the internet, then protecting this door is essential. IT companies and , ensuring DNS security is not a luxury, but an absolute need to maintain data integrity, business continuity and users' trust.
The importance of DNS security for companies and IT professionals
Ignoring DNS safety is like leaving the front door of your company unlocked and expect nothing to happen. The threats are real and the impacts can be severe. A robust cyber security strategy must include specific measures to protect infrastructure and DNS consultations.
Mechanisms and good protection practices
Fortunately, there are several tools and practices that we can adopt to strengthen the safety of DNS:
- DNSSEC (Domain Name System Security Extensions): Think of DNSSEC as a seal of authenticity for DNS answers. It uses digital signatures to ensure that DNS information received by your computer is genuine and has not been tampered with. The adoption of DNSSEC by both domain owners and DNS resolvers helps mitigate cache poisoning attacks.
- DNS Firewall and Content Filters: This is an extremely effective proactive protection layer. One DNS Firewall, often integrated with web content filter solutions, it works by inspecting DNS requests and blocking access to domains known to be malicious (hosting phishing, malware, control servers and botnets, etc.) even before the connection is established. In addition to safety, these tools can also be used to control access to websites that can be unproductive or inadequate for the work environment (social networks, games, adult content, etc.).
- Solutions like Lumiun DNS offer robust protective layers, acting as a proactive shield that filters threats even before they reach the company's network, ensuring safer and more productive navigation for teams, including remote work scenarios.
- DNS Query Monitoring: Analyzing DNS traffic logs can reveal suspicious patterns, such as a large volume of queries for unknown or malicious domains, indicating a possible malware infection or an attempted data exiltration via DNS Tunneling. Security Information and Event Management (SIEM) tools can help correlate these events.
- Use of reliable and insurance DNS resolvers: Opt to use DNS servers resolving reliable provider that implement good safety practices such as DNSSEC validation and protection against DDOS attacks. Many internet providers offer this, but public services like Cloudflare (1.1.1.1), Google (8.8.8.8) or Quad9 (9.9.9.9) are also good alternatives, focusing on security and privacy.
- Maintaining updated software and systems: This includes customer and server operating system, router and firewall firmware, and DNS servers software (such as Bind). Updates often correct known vulnerabilities that could be explored in attacks.
- Secure DNS servers: If you manage your own DNS servers, make sure they are configured correctly to prevent them from being used in amplification attacks (disabling recursion to external customers, for example) and protected against unauthorized access.
CONCLUSION: DNS as a modern internet pillar and network security
Our journey through the DNS universe has led us from the dawn of the internet, with the modest hosts.txt file, to the complex and vital infrastructure we have today. We saw as Paul Mockapetris revolutionized the way we connected, creating a hierarchical and distributed system that allowed the internet to climb to billions of users and devices.
We unveiled the “magic” behind a DNS query, understanding the role of each server in the translation of friendly names into IP addresses. We explore the numerous benefits that DNS gives us, from the simple ease of navigation to the viability of advanced services such as load balancing and CDNs.
However, we also face the dark side: the various threats that explore DNS, such as cache poisoning, kidnapping, DDOS attacks and tunneling, and the significant impact they can have. But more importantly, we have seen that there are mechanisms and good robust practices to protect this essential gateway to the Internet, especially DNSSEC solutions and DNS Firewalls, which act as proactive guardians of our navigation.
For you, IT professional, DNS is not just another protocol. It is a fundamental pillar of the modern internet and a critical component of the safety of any network. Understanding its functioning, its benefits and risks is essential for building and maintaining digital environments safer, resilient and efficient. That this knowledge enables you to be an even better architect of the security and performance of the networks under your responsibility, ensuring that the “invisible conductor” continues to govern the internet in a harmonious and protected way.
References
- RFC 1034: Domain Names - Concepts and Facilities
- RFC 1035: Domain Names - Implementation and Specification
- Cloudflare, Kaspersky, IBM, Microsoft on DNS and DNS DNS.
- Lumiun Blog Content on DNS Security and Content Filter.










