As the internet becomes increasingly present and relevant to business and professional activities, questions grow about how to maintain privacy and security online in a way that doesn't harm business. Storing personal information, private data, and company finances and keeping them protected can be difficult, but it is possible to avoid the vast majority of scams, spyware, and privacy breaches.
Therefore, we have put together some tips to help you determine if your company's internet is being used correctly by employees, avoiding threats, or if it is vulnerable to potential cyberattacks .
Website security check
Often, your employees may be browsing the internet looking for something, or simply passing the time if there's a internet usage policy , and end up "migrating" from site to site. This type of behavior can be detrimental to the company, considering security. Since there are countless websites available today, if security and reliability checks aren't performed, it's easy to fall into a trap.
Some websites request personal information to connect to your account or to complete a transaction. Hackers, thieves, and spyware programmers know this, and often try to intercept your information during these transactions. Therefore, always use secure websites and companies and demand that access rules are properly followed by your team.
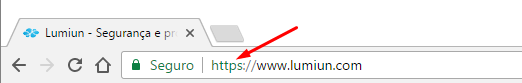
First and foremost, you should only give your information to reputable companies, and then check if the company's website uses a web address that starts with "https" and if it has a padlock symbol in the address bar or at the bottom of the browser. This means that the website encrypts your information, virtually rendering the data useless to any thief or hacker who might intercept the transmission.
Nothing is free
Is the internet full of good people wanting to offer wonderful and irresistible gifts and deals? Rarely. Often, a tempting contest appears on social media with the chance to win various technology products or even ads promising to deliver gifts or freebies to your home.
It's important to be wary of these types of campaigns, as many of these promotions require you to fill out a registration form with personal information in order to participate. These contests tend to excite people, so in the workplace it can be important to monitor what employees access, to avoid putting confidential company data at risk.
Cybercriminals use these attacks to gather information that can be used in identity theft attacks. It's important to know that these hackers are constantly searching for something, in this case, a network to infect.
There is also ransomware, which is a type of malicious software (malware) created with the intention of blocking access to files or systems, only releasing them after payment of a specified amount. It's like a virtual kidnapping. Although seen as a recent security problem, ransomware is not a new concept: the first references to this type of digital plague date back to the late 1980s.
Qualified passwords
Many people use passwords that are easy to remember, or that resemble dates like birthdates, someone's birthday, or numbers like "123456". Most of the time, this isn't the best option. From email to social media, and even online banking, passwords are an essential component of our online lives. Passwords should protect our information from unwanted access. The stronger the password, the harder it is to crack.
This concern about strong passwords needs to come from all employees, not just those who access more important information, such as bank details. A report by SplashData revealed that many people used easy and very dangerous passwords in 2016. Find out which were the 25 most used passwords in the world in 2016. If you want to protect yourself more effectively by using secure and stronger passwords, you can check out our guide to creating and managing user accounts and secure passwords . With it, you will learn a set of rules and actions to create and manage passwords in the best way, reducing the chance of them being discovered and consequently attacks and threats.
Identifying fake emails
Are you receiving emails claiming you owe money to a phone company, alleging one of your documents is illegal, or offering prizes or virtual love cards? Are you being summoned to a court hearing? Do you receive supposedly important news about a famous person? It's likely spam , meaning a fake email.
If the message contains spelling and grammatical errors, makes tempting offers, or has a link different from the one indicated (to check the real link, simply hover your mouse over it, but without clicking), be immediately suspicious. If in doubt, contact the company whose name was mentioned in the email.
When using corporate email, it's important to be extra careful because employees may unknowingly open spam emails simply because they appear to contain something important. In such cases, informing employees or offering tips, such as checking the sender's address, can be helpful.
Program updates
It's also important to keep your company's programs updated. Many people think that new versions only add features, but the truth is that they also include fixes for security flaws. Therefore, always use the latest version of your programs, especially those that access the internet (web browsers, email clients, etc.). Many applications have a feature that automatically updates the program or notifies you of new version releases. It's a good habit to leave this feature enabled.
Do you have any type of monitoring or security software?
It's a great option for those willing to invest money in controlling threats and keeping their network more secure. Companies that work with sensitive data and can't monitor each employee individually can opt for internet control . This type of solution helps to make the network more secure and keeps track of what each employee is accessing within the company network. This allows the owner to manage and know if employees are accessing harmful websites that could damage or put the company at risk.
Try some of the tips mentioned above. Share your experience with us and stay tuned for more internet safety tips!












3 comments
Comments closed