In short, we can understand information security as protection against unauthorized use or access to information.
Considering that information is one of the most valuable goods in an institution or business, it is essential to maximize the risks of leakage or loss of data, files or database, human or operational errors, misuse of systems due to lack of training, network stops or services, information theft or any other threat that may harm the company.
Information security is not limited to computer systems or information in digital format. Because the concept applies to all aspects of information protection or data, in the various possible forms. The level of protection must correspond to the value/importance of this information and the losses that could result from the improper use of the data. It is also necessary to remember that information security covers all infrastructure that allows its use, such as processes, equipment, systems, services, technologies, and others.
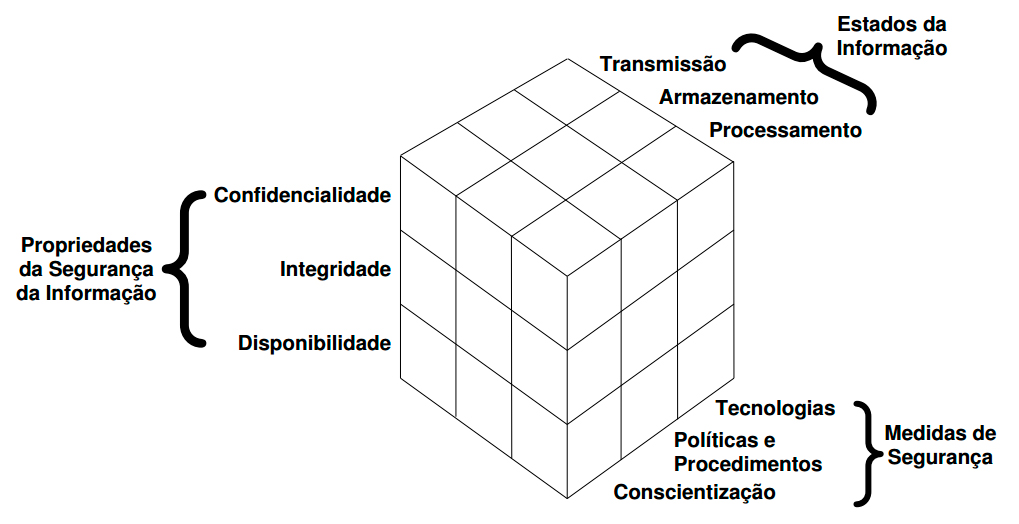
In security, we have three principles that underlie and guide the analysis, planning and implementation of security in companies that wish to protect their information, which are: confidentiality , integrity and availability . In addition, other important attributes are irreversibility , authenticity and compliance. Privacy also demands great concern, considering the evolution of e -commerce and the information society.
Confidentiality
It consists in ensuring that information will be accessible only to persons/entities with permission defined by the person responsible. At the same time the information must be protected for any form of unauthorized access. Loss of confidentiality occurs when someone unauthorized obtains access to resources/information.
Integrity
There should be guarantee that the information remains with all the original characteristics defined by the owner of the information, including actions throughout the data life cycle (creation, maintenance, editing and destruction). We have the loss of integrity when the information is improperly changed or when the data cannot be guaranteed updated, for example.
Availability
It is the warranty that information is available for access at the desired moment. It corresponds to the effectiveness of the system, the correct operation of the network so that when the information is necessary it can be accessed. Lack of availability occurs when access is desired and expected access is not possible.
Other important concepts in information security are:
- Authenticity : Guarantee of identification of the source declared as arising from the information and that the data has not undergone changes throughout a process.
- Irreversability : must ensure the impossibility of denial of authorship in relation to a transaction performed.
- Compliance : Ensures that the system is in accordance with the laws and regulations associated with the type of process.
- Privacy : exposure and availability of information should be controlled according to the content and importance of data
We can see that the concepts that underlie information security are broad and complement each other. Thus, companies need to look for their security policy actions that meet all these concepts, as vulnerabilities and threats to information security are directly related to the loss of any of the three main security features.
For the elaboration of a security policy, the risks associated with lack of safety ; the benefits and advantages and the costs of implementing the mechanisms . The investment can become high, but the risk and occurrence of security problems can cost companies much more.












1 comment
Comments closed