Have you heard of phishing ? Although the internet brings many advantages and facilities to our routine, it is also full of threats to the security of your information . False sites, corrupted banners, fake emails, SMS with malicious links. All of this can be a true trap for the security of your devices and confidentiality of your data.
One of the tactics used by cybercriminals is the so -called phishing attack. This strategy consists of a technique that plants baits and traps to collect information fraudulently to use this data in frauds and financial blows.
How is phishing applied?
There are several ways to apply phishing today. Here are the main tactics used by criminals:
- Common Fishing;
- Spear phishing;
- Phishing clone;
- Whaling;
- Vishing and Smissioning;
- Phishing through social media.
What will differentiate the type of phishing attack will be the channel to be used and the targets to which the approach will be directed. Unlike what you think, a phishing attack doesn't just happen by email: it can come through voice calls, SMS services, fake websites, social networks, and many others.
Because of this wide variety, it is essential to be very careful with any suspicious content to avoid the leakage of data and financial blows.
What is the origin of this type of coup?
Although it seems to be a type of recent trap, phishing has been applied since the 1990s . Initially, phishing attacks were used to steal and defraud AOL - America Online accounts, an internet service provider that pioneered this branch. The portal remained active in Brazil until mid -2008.
Using methods to find accounts and credit card numbers , criminals were fraudulent passwords and diverted information. As internet was still a very difficult resource to obtain at the time, it was necessary to pay a fee, and many users could not pay for access.
In order to increase your sales, AOL has started providing a free 30-day test, which ended up attracting bad faith users who would like to continue using the service for free. In order for them to continue accessing free, cybercriminals began to steal accounts of legitimate users to maintain their access .
How can it harm your business?
The phishing attack is a strategy that is nonetheless practiced by cybercriminals, as it can still be very efficient. Differently the attacks involving installation of software and malicious applications, the phishing attack uses the user's own vulnerability so that they succeed.
If for an individual data loss can represent a great damage, for a company losses can be alarming and catastrophic . This type of attack can cause many consequences for a business, such as:
- Loss of reliability towards consumers: Companies that expose the confidential information of their customers and suppliers, even because of a cyber attack, may lose their reliability in the market.
- Loss of competitiveness: When it comes to competitiveness, the safer the information is, the more well positioned the company will be.
- Unavailability of information: Some phishing attacks may favor even more aggressive attacks, such as ransomware . In this type of strategy, cybercriminals “kidnap” data or provide systems, requiring the payment of a “rescue” to return this information.
- Financial Loss: Depending on the consequences of the attack, it may be necessary to invest in solutions to mitigate the damage caused, make redemption payment to recover the information, and even bear indemnities for customer customer clients.
What to do in the face of such an attack?
The first tip to be given to avoid falling into the phishing traps is: If you receive an email, SMS and a suspicious social network message, do not open. To be able to identify such traps, it is very important to stay aware of the signs that this information is not true.
See below a very common example of phishing “bait”:
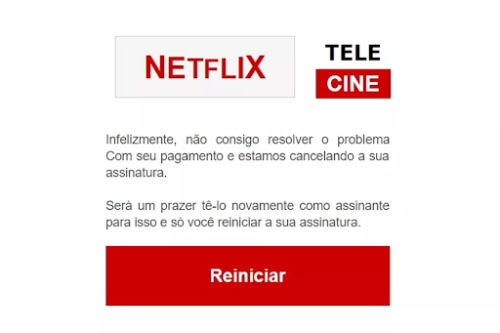
Realize that a disadvantaged user looks quickly and does not realize that this is a bait for a phishing attack.
Within the company, if a user receives some kind of notification that seems malicious or suspicious, it is of utmost importance that they contact the responsible IT team . If for some reason the employee access a link, or enter information on a website that may be fraudulent, it is essential that the fact be warned to those responsible, so that security measures are taken as soon as possible.
To try to keep your employees away from this kind of problem, your business can count on an Internet access control system to manage more assertively as accesses have been made in the company. This type of tool helps from preventing users from having access to dangerous pages indiscriminately and putting the confidentiality of information at risk.
Do you know how the internet security is on your business? Click here and make a free diagnosis of your business situation!









