When you are a company's IT analyst or director, it is important to make some important decisions of network control and safety. Especially when the internet is the main tool for the company's full operation. If this responsibility were not enough, the volume and sophistication of cyber attacks that aim to harm organizations grow more and more. Therefore, it is relevant for professionals in the field to be aware of tools that can assist in blocking these attacks to avoid loss of information, productivity and money.
In addition, the network security investment budget and internet control is always limited to most small and medium -sized companies. Therefore, it is necessary to study the entire scenario of the network, act quickly and find an integrated solution to improve digital security without exceeding excessively and not overloading team productivity.
One of the most important parts in the network, because it is mostly the gateway to the attacks, is the DNS layer. And with an integrated solution, which uses data intelligence and studies the reputation of each site it is possible to identify and block malicious sites such as access anonymitors, hacking, keylogger, malware, spyware, phishing and fraud. Thus, a solution that helps protect the DNS layer from a company's network becomes the first line of defense, as DNS requests precede all activities on the Internet.
Main types of attacks on the DNS layer
It is not just companies that create safety solutions that are innovative. Cyber criminals, out of necessity, also aggressively innovate trying to find loopholes and safety policies of organizations.
But in recent years, criminals have become more motivated and ambitious due to the growing financial rewards arising from "happy" end attacks. As the digital environment is increasingly used, generating a lot of important information, the data of these companies become valuable and the main target of these criminals. If this data is stolen, it can be resold in the open field on the Internet for a very significant value. Another type of attack is increasingly common ransomware
The most common DNS attack techniques make the user try to access a certain page and be directed to an incorrect destination. These techniques are called cache poisoning (DNS) and server (DNS Hijacking).
The DNS Poisoning attack occurs when a criminal can infiltrate the DNS server, with the purpose of modifying the information recorded in the cache and thereby changing the destination IP number without changing the address the user types in the browser.
The DNS Hijacking attack, the criminal uses malware to kidnap domain translation requests and redirect traffic to a malicious DNS server.
The difference between the two techniques is that the focus of the criminal in the first (DNS poisoning) is the DNS server and the second (DNS hijacking) is the device itself (computer, laptop).
Malicious pages to whom the user can be directed are generally cloned (a phishing ) in order to disseminate malware loads or unwanted applications, mining cryptocurrencies, steal information on counterfeit access forms, etc. And as the user typed the correct domain, he will hardly identify agile that he was the victim of this type of engineering.
Advantages of DNS layer control
A solution for controlling DNS requests bring many advantages to companies, which we highlight the following:
-
- Safety internet access control solution, proactive protection against emerging threats can be made. These solutions are equipped with services that have constantly updated suspicious websites. Another important feature is the possibility of defining the necessary reputation level that a site must have to be accessible on the network, making the lock if the level is lower than the configured.
- Productivity : The misuse of the internet by employees can greatly compromise the productivity of the company. This waste of time can occur in countless ways, access to social networks such as Facebook or Instagram, access to personal email, communication services such as WhatsApp or Skype, entertainment sites, shopping, sports, among others. However, an Internet access control solution also allows blocking unwanted websites that are outside the company's scope and causing employee time waste and compromise productivity.
- Cost reduction : With increasing network safety, decreasing equipment maintenance costs and increasing team productivity, investment in an internet access control solution often pays in the first months.
- Information : Another important point is the gathering of information about the use of the internet, having reports of what is being accessed, and analyzing this information together with team productivity reports and task delivery, can lead to the optimization of your internet access policy.
Tools to increase network security
As the DNS layer is the door to major cyber attacks on a company's network, the implementation of a tool to increase security becomes an essential factor to ensure information security.
By preventively blocking all requests in any port or protocol, safety in the DNS layer can interrupt the action and avoid the burden of identifying the specific origin of that attack.
To increase network safety in your company, there are different alternatives, such as traditional proxy Linux solutions provided by specialized companies, which require greater investment with servers, specialized labor and constant maintenance.
Other options are Sonicwall , Fortinet Fortigate and the like, or more modern solutions that use cloud resources and are more affordable, easy to implement and management. This type of service is mainly recommended for small and medium businesses, good options are Lumiun , OpenDNS or DNSFilter .
To choose the best option to manage internet access, it is important to define your business needs well and compare the costs, features and benefits of each of the existing solutions.
Why Lumiun?
The company Lumiun is the only one of the options mentioned above that is 100% Brazilian. We really understand how the work environment works in Brazilian companies and create solutions that can increase network safety and team productivity.
There are more than 22 million controlled accesses daily and 3.2 million unwanted hits blocked. It is data we study and that we agreed with third party services with the intention and commitment to protect the company's information.
Main features you find at Lumun:
- Access control:
- Release and block of applications, websites and categories of websites. Including for time;
- Protected search ( safesearch ) on Google, Bing and Youtube to ensure that inappropriate content are not displayed in the results of the search;
- Domain research where Lumiun scanns and finds its category, reputation, description, last accesses and a preview of the page.
- Security:
- Option to define the minimum reputation level to access a site;
- Blocking sites that belong to categories considered harmful such as hacking, malware, phishing, etc.
- firewall:
- Forget the old concept and difficult to implement firewall rules on your network. In Lumiun it is possible, with few clicks, to add blocking rules and release by doors, protocols, origin and destination. In addition, there are predefined settings that help the most lay people on the subject.
- Speed:
- With this feature you can limit the amount of download and upload to equipment groups. This way you can distribute your internet link as you find it better or according to the demand of each group.
- Reports:
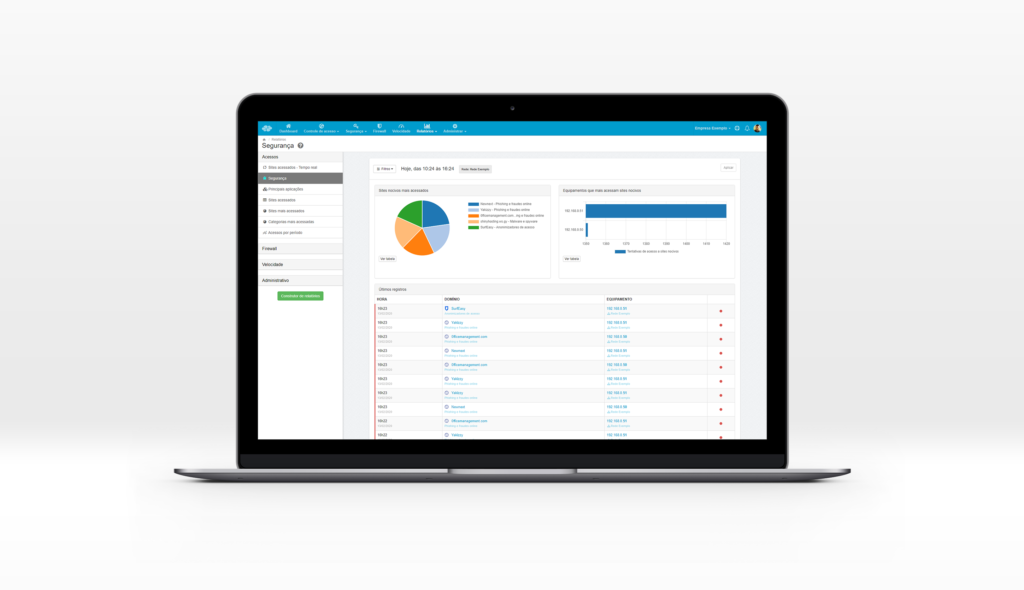
- There is no point in all these resources if it was not possible to follow the result. At Lumun you can track in real time which are the most accessed or locked sites, access per period, safety blocks, firewall logs, equipment that most consumes the band on the internet and more.
What customers like most at Lumiun is the ease of multi -net management in a single control panel, simple and accessible from anywhere.
20 minutes to increase network safety in your company
After passing on our main features and benefits, you may be apprehensive that you think it is a complex solution that takes time to deploy and has a high cost.
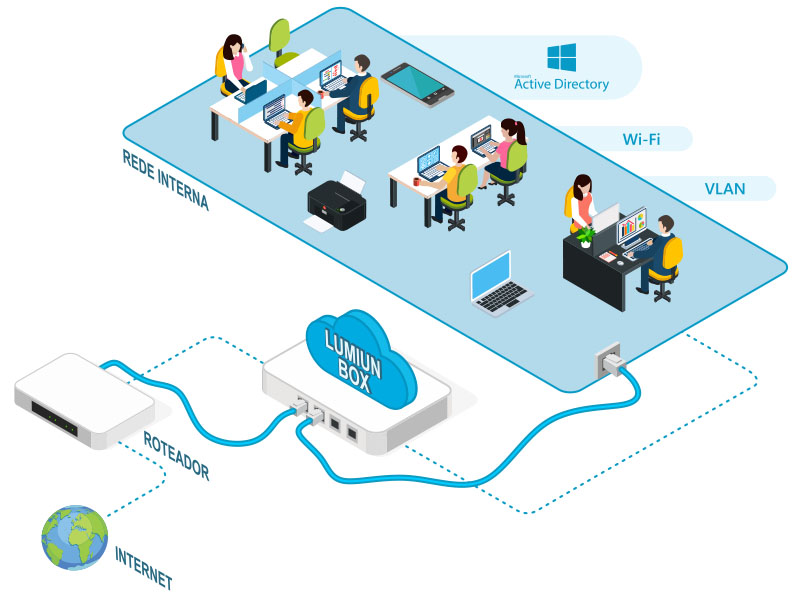
Good news! After receiving the Lumiun Box (sent in lending), our service team assists you at all stages. On average, since the installation of the box on the network and configuration of the control panel, our customers take up to 20 minutes. It is only 20 minutes to make your company's network safer and your team more productive.
In addition to Lumiun Box , there is yet another solution, which does not need equipment and reduced cost, Lumiun DNS , see more here .
What about the cost to hire Lumiun? You will be impressed by the low investment. Request our contact on the form below or go to www.lumiun.com .












2 comments
Comments closed