Rapid vulnerability patching is no longer just a good practice; it's now essential for protecting your company against increasingly fast and sophisticated cyberattacks. According to 2024 data, 23.6% of known vulnerabilities were exploited on the same day or before official disclosure , according to VulnCheck . Given this scenario, rapid responses and effective risk mitigation strategies are crucial.
Although many organizations still face challenges , it is entirely possible to accelerate the remediation of vulnerabilities with more efficient processes, modern technology, and a strategic security vision.
Throughout this article, you will discover how to transform this process into a competitive advantage using three fundamental pillars: automation, risk-based prioritization, and proactive protection technologies such as secure DNS .
Why do security flaws continue to be exploited?
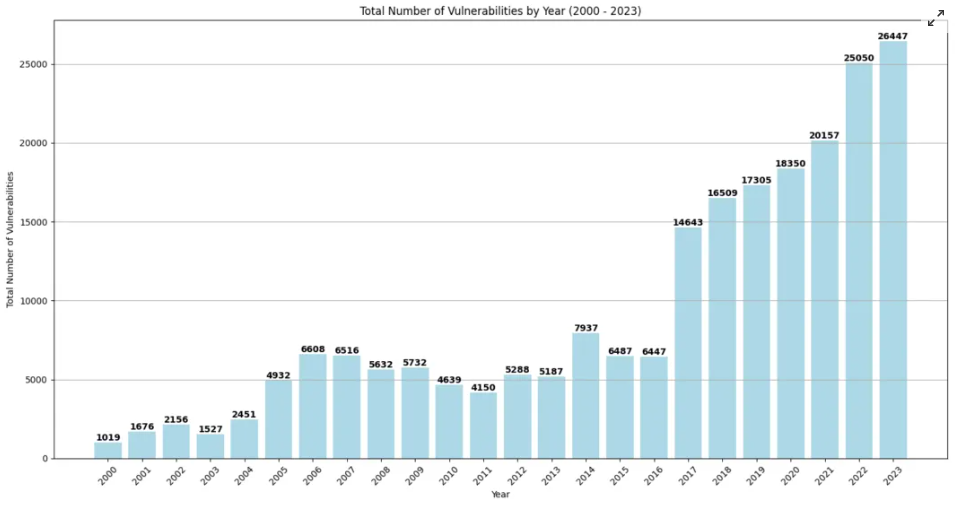
In 2023, more than 26,000 vulnerabilities were reported , according to CVE Details. On the other hand, despite this growth, the good news is that the tools and techniques for dealing with this volume have also evolved significantly , offering companies new protection possibilities.
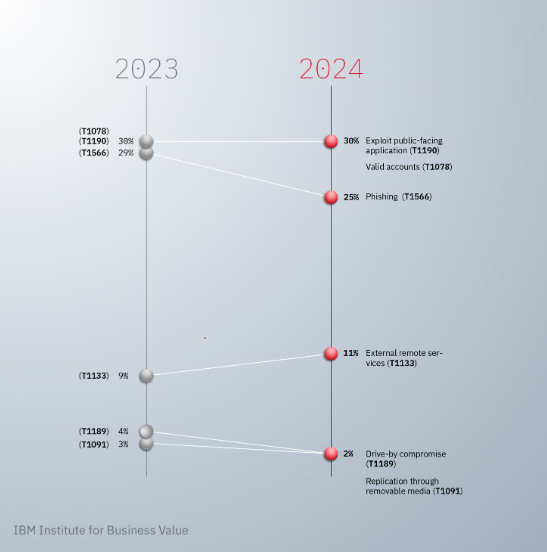
Furthermore, according to the IBM X-Force Threat Intelligence Index 2024 , the use of valid credentials was the primary vector for initial access in cyberattacks, accounting for 30% of the incidents analyzed , alongside phishing .
With best practices and the use of automation, vulnerability remediation becomes a simpler, more reliable, and more effective process.
Key challenges for patching vulnerabilities:
- Lack of visibility into existing vulnerabilities: Complex IT environments—including cloud , containers , and multiple devices —naturally make it difficult to maintain an accurate inventory of assets and their respective vulnerabilities . Furthermore, outdated tools, infrequent scans, and non-integrated systems contribute to this problem, hindering a quick and effective response.
- Dependence on time-consuming manual processes: Manual vulnerability management involves slow and error-prone tasks such as scans , result triage , ticket opening , and patch application . Therefore, this process does not keep pace with the speed at which new vulnerabilities emerge and are exploited, ultimately increasing the risk of successful attacks.
- Lack of proper prioritization of fixes: not all vulnerabilities present the same level of risk . However, without a risk-based approach, teams may waste time fixing low-impact flaws , while critical threats remain exposed . Furthermore, the absence of prioritization frameworks and effective communication between security teams and business areas exacerbates this situation.
How to accelerate vulnerability remediation in your company.
To mitigate the risks associated with unpatched flaws , companies must and data-driven approach to managing vulnerabilities . In this sense, three pillars underpin this transformation: automation and continuous monitoring , intelligent prioritization , and the use of DNS-based protection technologies .
1. Automation and continuous monitoring
Automation allows the company to transition from one-off analyses to a continuous security posture. To achieve this, advanced tools perform constant scans of networks , systems , and cloud environments , automatically applying patches or generating real-time alerts .
Furthermore, continuous monitoring ensures an up-to-date view of security, allowing for the rapid detection and action on vulnerabilities or misconfigurations . Finally, the integration between vulnerability scanning and asset management adds context and improves prioritization.
Benefits of automation:
- Reduction in incident response time
- Reduced manual effort from the IT team.
- Greater consistency in patch application.
Solutions like Lumiun DNS help monitor access and block malicious websites , preventing threats from reaching vulnerable users or systems. Furthermore, DNS-level security is an additional layer of defense that acts preventively, even before vulnerability exploitation , reducing the attack surface and protecting the network against malicious domains and command and control servers.
2. Prioritization of critical fixes
Adopting a risk-based vulnerability management approach is essential for optimizing security resources. In this context, using classifications such as the CVSS (Common Vulnerability Scoring System) allows for an objective assessment of the potential impact of each vulnerability.
Furthermore, effective prioritization must consider the criticality of the affected asset, the sensitivity of the data, the existence of active exploits, and the availability of patches. This strategic approach ensures that remediation efforts are directed at the most dangerous threats to the business.
Good prioritization practices:
- Assess the potential impact of each failure.
- Prioritize vulnerabilities with known publicly available exploits.
- Fix the most critical systems first.
The use of detailed reports and intelligent blocking policies —such as firewalls and prevention systems—also complements prioritization, offering temporary protection while fixes are applied. In this way, the combination of visibility, data, and agile actions strengthens the company's security posture.
3. Artificial intelligence as an ally in prevention
AI and machine learning-based solutions enable security teams to identify suspicious patterns, detect emerging vulnerabilities, and anticipate threats before they materialize.
How AI strengthens vulnerability remediation:
- Anticipating malicious behavior
- Identifying flaws before public disclosure.
- Real-time anomaly detection
Conclusion: Turn security into a competitive advantage.
Patching vulnerabilities is more than an obligation: it's an opportunity to evolve, protect data more efficiently, and strengthen trust in your IT infrastructure.
Furthermore, with the support of modern tools like Lumiun DNS, your company can act quickly, keep the network protected, and face digital security challenges with confidence.
Start strengthening your company's security now with smart solutions like Lumiun DNS. Fixing vulnerabilities can be simple, quick, and strategic.









