In the digital world, cybercriminals are always looking for new ways to apply virtual blows and commit online fraud . Using increasingly sophisticated techniques, these attacks become difficult to identify - and one of the most common methods is called spoofing .
Spoofing is a digital forgery technique used to deceive users and systems, making it appear that communication comes from a reliable source . This type of attack can be used for data theft, invasions and dissemination of malware, among other malicious goals.
With increasing threats in the virtual environment, understanding how spoofing works and what its main variations are essential to reinforce digital security and protecting itself against damage.
In this article, we explain what spoofing is, how it is applied and what you can do to avoid being a victim of this type of scam.
What is spoofing?
Spoofing is a type of cyber attack in which a digital criminal falsifies his identity to deceive the victim. This can occur through emails, telephone calls, IP addresses, fake websites and even signs of GPs. The goal is to induce the person to provide sensitive data, click malicious links or install hazardous software.
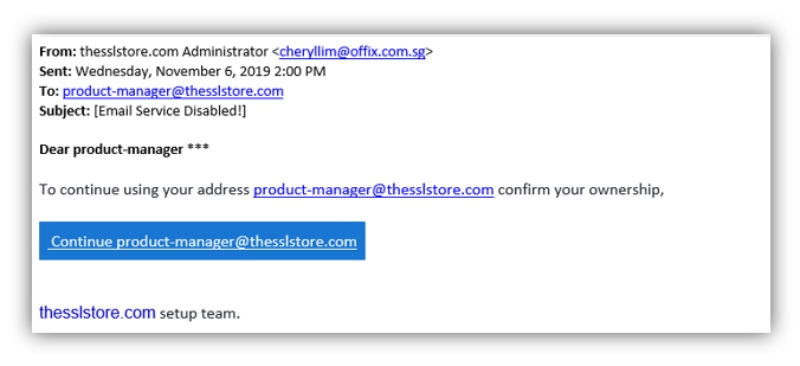
Although contact information such as name, header and email looks real, the content is doubtful. Often, this email asks you to access suspicious links or provide information that is not really in the interest of this contact . With this we can suspect that it is an attempted spoofing attack.
Many people confuse the practice of spoofing with phishing because of some similarities between them . To clarify, we will deal with the differences between these two approaches throughout this article. But it is important to clarify that spoofing uses address mask to be able to deceive its victims. Understand how this works: spoofing
In order to be successful, the spoofing attack depends on the cybercriminal ability to pass through a company or confidence person of your victim, simulating your contact information, such as the email address or telephone . It tries to make you trust the legitimacy of this contact and provide the confidential information that will be used in the application of future blows.
Although it is a practice applied many years ago, the spoofing blow gained a lot of visibility from 2019, when the technique was used to hack politics . The operation implemented by the Federal Police to identify the cybercriminals involved in the attack was known as Operation Spoofing.
The following year the maneuver gained even more popularity, reaching several people. Because of this, Procon began to issue alerts to users who received calls from their telephone number in scam attempts.
How does spoofing work in practice?
As we have seen, cybercriminals spoofing techniques to pass for reliable people or companies, with the aim of deceiving their victims and getting sensitive information. These attacks can happen through different channels, such as email , SMS messages , or telephone calls .
A classic example of social engineering is the scam of false kidnapping: the criminal pretends to be a relative of the victim and convinces her that she is in danger, demanding the payment of a ransom. Although the kidnapping is not real, urgency and emotional appeal make the blow effective.
In the case of spoofing , the principle is the same - but it occurs in the digital environment. Criminals disguise digitally to seem reliable, inducing the victim to reveal confidential data , install malware or even make bank transfers .
Because it is based on falsification of digital identity , spoofing is difficult to identify and can cause serious financial losses and compromise data security.
Spoofing Types
As we saw earlier, the spoofing blow can be applied through various channels and resources. We will see below what are the main ways that cybercriminals use to attack their victims:
Email spoofing
This is the most commonly used form for spoofing blow attempts. Normally, this type of scam involves requests for personal data or financial information, such as passwords and credit card numbers.
For the victim to believe in the legitimacy of the request, the criminals seek to disguise themselves as reliable referrals, conviviality or knowledge of the victim. Thus, there is a presumption of legitimacy , which causes the user to provide the requested information without knowing that they are being referred to a criminal.
Another imminent risk in the email spoofing is the corrupted or malicious attachments that accompany them. Often these emails are forwarding malware and viruses , which can hinder the safety of their devices and favor hacker entry.
In order to succeed in their approach, cybercriminals use social engineering to more efficiently achieve their victims . Do you know how social engineering applied to cyber attacks works? Check out this material and better understand this kind of strategy.
IP spoofing
In the case of IP spoofing, the main focus is on networks, and non -users, where the criminal seeks access to a system. By sending messages using a disguised or false IP , it tries to disguise you from a user of the same network for access to be granted.
For this to be possible, the cybercriminal uses a legitimate IP, changing the headers of the packages that are sent . Thus, requests seem to have come from a reliable device.
When you get access, it can divert visitors from a legitimate page to a fraudulent website, enabling the collection of sensitive information or the application of substantial financial blows. This approach is known as websites spoofing.
DNS Spoofing
This approach works similar to IP spoofing. However, in this case the cybercriminal seeks to manipulate network connections , also diverting access from users from legitimate pages for fake websites.
Also known as cache poisoning, this type of virtual attack takes advantage of vulnerabilities on domain name servers so that, illegitimately, divert the real traffic to false pages.
Call Spoofing and SMS
This attack is quite simple to understand, as we become aware of various approaches of this kind almost daily. Cybercriminosus uses the connection, SMS or message platforms , passing through a company or legitimate contact as a way to apply their blows.
Simply put, the telephone spoofing uses false call identifier to hide the true origin of a telephone call . For this, cybercriminals are looking for ways to make their number as similar as possible to the number of a real company. Thus, the greater the chances of the connection to be answered.
Spoofing x phishing
Phishing be considered as an evolution of spoofing. often apply phishing blows use the spoofing technique to disguise and deceive their victims, leading them to believe that content or attempted contact is legitimate.
We can understand spoofing as a broader technique, as is the case with IP or DNS address spoofing. In this case, the criminal uses methods and technical tools to deceive not users, but a complete system or a computer. For this reason, spoofing and phishing attacks are considered very similar approaches and are often used in line.
Is it possible to protect yourself?
The first step in protecting itself against cyber threats is to become aware of its existence and the need to implement security strategies and protocols.
It is extremely important to know what threats are around the digital world to identify possible attempts at scam and fraud. Although confidence is a very positive aspect, overconfidence can lead us to blows into various types , impairing the confidentiality of our information and favoring various types of threats.
In the case of spoofing, it is essential:
- Pay attention to the legitimacy of emails that are received, as well as telephone calls and SMS;
- Be careful when accessing links to suspicious emails, because in most cases these links redirect to false or fraudulent pages;
- Do not download attachments without prior analysis as they may be contaminated files that impair the operation of your device ;
- Security tools that help you increase your devices protection, such as antiviruses and spam blockers , are essential.
Although IP spoofing is easier to identify, DNS spoofing is more difficult to combat, requiring some technical knowledge to avoid this type of scam . Learn how to check your router DNS through this tutorial .
Another very important aspect is to distrust the requests made in emails, such as personal document requests, credit card numbers and passwords, security codes, among others . Whenever possible, seek to activate two steps in your email services, preferably without using phone number or SMS service as a second safety layer.
We have a complete material to help you increase the safety of your email, check it out here !
How Lumiun DNS can help protect your business from Spoofing
Lumiun Lumiun DNS DNS -based network security solution that operates in preventing malicious content and fake sites, often used in spoofing , phishing and other digital threats.
By using Lumiun DNS, all the company's network navigation goes through intelligent filters, which automatically identify and block hazardous or suspicious domains, even before the user has a chance to interact with the threat. This significantly reduces the risk that employees are deceived by counterfeit sites or disguised malicious links.
In addition, Lumiun DNS offers:
- Constant updates on threat lists , based on reliable sources and artificial intelligence;
- Detailed reports of locked access and suspicious activities on the network;
- Content control , allowing the company to define permitted or restricted websites categories;
- Protection for local networks and employees in home office , ensuring security wherever they are connected.
By adopting Lumiun DNS , your company raises the level of digital security , minimizes risks and strengthens preventing increasingly sophisticated blows.
Lumiun Box: The ideal tool for companies
Aimed at companies, Lumiun Box can be the ideal tool for protecting spoofing and phishing in organizations . internet access blocking solutions , Lumiun Box prevents malicious websites from being accessed, as well as malware files sent by email for example. In addition, it is possible to determine access policies for certain groups, making the use of the company's internet network much safer and healthier .
See some benefits of using the solution in the business environment:
- Security
- Network firewall, protection against harmful websites, business VPN and lower risk of information loss and viruses
- Productivity
- Control the accesses! More focus on activities relevant to the company and less wasted on the internet
- Cost reduction
- Decrease in equipment maintenance costs, virus problems and team time waste
- Information
- Graphs and reports of the websites and services that are being accessed by employees
In addition to the site block features, Lumiun Box has some others, see:
- Business Firewall;
- Business VPN;
- Management Reports;
- Traffic Management;
You can see caracateristics of each feature through the website www.lumiun.com/ box , or making a free demonstration .
Do not only let luck protect your business data and information. Use effective and focused protective tools for your need .