Internet access is part of the corporate world and it is virtually impossible to think of success or growth without this fundamental resource. Although it is a tool that delivers practicality and quality to the tasks that are performed, the internet is also a risk environment that can impair employee productivity . For this reason, the creation of an Internet Access Control Policy becomes fundamental to companies that want to achieve their success and bring higher results.
From small businesses to large corporations, productivity loss is a recurring problem. With such a large and content and information environment, the internet ends up excessively distracting employees and making the time that should be destined for the company's relevant activities to be busy with improper access.
In addition to considerably damaging productivity, indiscriminate internet access can cause security problems for the company . There are several traps in the digital environment planted to attract users to apply scams such as data theft, financial blows, data kidnapping, among other threats.
Cyber attacks have been causing immense damage to companies of all sizes and segments. With increasing digital trade , DDOS type attacks showed meteoric growth, causing business to lose profitability and market positioning . Do you know how this kind of cyber attack works? Check out this explanatory video:
That is, unrestricted internet access wastes resources and increases the risk of cybers . Access control emerges as an essential tool for increasing business compliance and contributing to smarter data processing.
Undue access to the Internet, in addition to wasting fundamental resources from the company and increasing the risk of cybership, also impact employee productivity and, consequently, on their market growth.
With that in mind, we have prepared this material with important information and key tips to help you create an efficient internet access control policy for your business. This way you can guarantee smarter use of your business resources and also increase your profitability.
Internet Access Control Policy: How does it work?
Within a company, employees must have access to all the resources and tools necessary to perform their tasks. Any access that is not effectively linked to professional activity can be a waste of resources and a great damage to the employee's productivity.
In this sense, the best way to ensure that this employee has focus and attention to the tasks in charge of being providing a distraction -free environment. Because of this, the implementation of an internet access control policy is nothing less than fundamental for companies that are seeking to add value and increase the productivity of their employees.
After the emergence of the General Data Protection Law , this agenda became even more relevant. This is because most companies deal with user information storage from users, customers and suppliers, and this information should be protected at any cost, ensuring the confidentiality of data that is stored, used and manipulated by a company.
With so many traps present on the internet, it is very important to have all the resources and strategies that help keep cybercriminals away from the relevant and confidential data of a business. Just as technology advances every day, the ways of stealing information, applying scams and hijacking data, so that the more prepared your business is, the safer it will keep up.
In the market, access control can be done in different ways, such as:
- Internet access control
- System access control;
- Control of access to files and documents;
- Network access control.
Performing the correct management of these resources, the company can increase its safety and ensure that its employees remain focused on the strategy and demand that is really essential to the business.
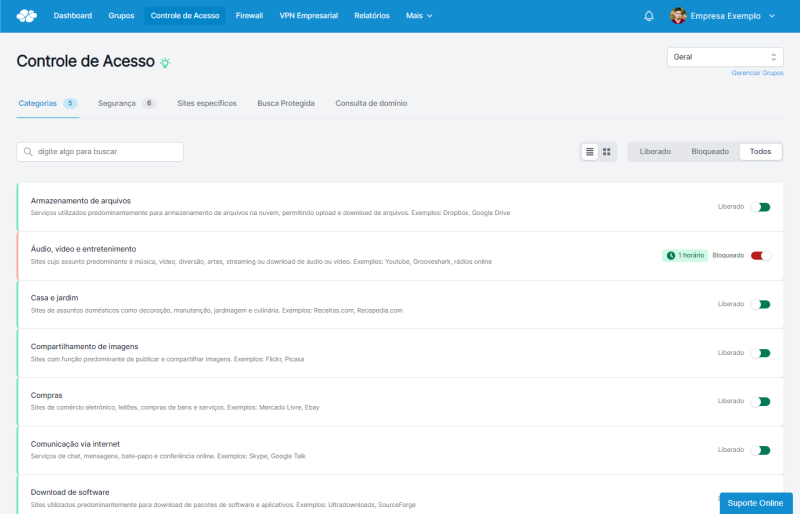
Internet access control policy is a tool focused on more efficient management of this valuable company resource. Through the correct tool, managers are able to control user access and ensure that only fundamental resources are used during working hours.
This does not mean that the company is being invasive or overly controlling its employees. The main objective of this strategy is to ensure that non -fundamental resources do not cause distractions and interruptions during the work routine and take the time of company employees. This happens a lot with access to entertainment sites, social networks, e-commerce, personal emails, among others.
6 Essential Tips
Now that we understand what an Internet Access Control Policy is and what your main goal is within the company, we will deal with some tips we have prepared for you to be able to implement this policy more efficiently within your business.
1. Understand how internet access works within your business
The first step is to map the type of access that is relevant to your business strategy. Managers need to establish which tools and resources need to be used to continue the activities. Based on this, it is possible to understand the behavior of users and from there establish more specific and efficient access rules .
This access mapping needs to inform what are the essential resources for performing the company's tasks, such as websites, applications and online tools. It should also contain access demands for each of these applications in order to avoid unnecessary access to confidential information.
2. Know the access standards
To be able to define more specific access rules, it is initially necessary to track user access standards. Thus, managers will be able to determine which features, websites, and tools should be blocked in order to obtain more effective access control.
Different users have different access patterns. Knowing the type of navigation that each user performs helps to establish smarter control and monitoring.
3. Determine a password creation policy
Password vulnerabilities are the main causes of vulnerability points that favor the incidence of a cyber attack today. This is because many people still use an obvious combination of passwords that can be easily guessed by the cybercriminal. Your team needs to be aware that passwords must be safe and difficult to deduct so that stored information remains safe.
4. Establish a training process
It is natural that in a company where the internet has always been released, blocking certain resources cause some strangeness from the team. Therefore, before implementing this policy, talk to your employees and explain the reasons for which this measure will be taken . They need to be aware of the importance of access control and how improper access can impact the results of a business.
5. Perform constant monitoring
Monitoring is essential to ensure that the rules created are being applied and followed as expected. This phase can be complex for managers when the lock is done manually, and for this reason, it is necessary to have an intelligent tool that helps in creating custom access rules and facilitates efficient monitoring .
Lumiun provides customizable and easy -to -use tools , being the ideal partner for your business. Delivering excellent value for money and simplified platform, we can help you increase productivity within your business.
6. Information Security Training is important
More urgent than just requesting safer password creation and stimulating smarter behavior in the online environment, it is essential that employees understand the risks and consequences that can be caused by a cyber attack. Establishing a program that helps employees better understand digital security and these threats can greatly help in the implementation process.
For you to find out how your business safety is, test with our exclusive diagnostic tool . Based on the report, you can find out what you can change in your business and increase the security of stored data.
5 advantages of implementing an internet access policy
As we have seen throughout this material, improper use of the internet can cause various damage to the business. Because of this, the implementation of an Internet Access Control Policy helps to ensure a variety of business benefits, as we will see below.
Increased productivity and quality of tasks
Without the distractions brought by improper access on the Internet, employees can deliver their tasks with agility and quality, improving their results during the work routine.
Focus on important tasks
Social networks, personal emails, e-commerce, news sites and entertainment. All of this represents a great flow of time available for work. Once this type of access was blocked, employees can work more focused on tasks that are really important for business continuity.
Digital security
There are several traps on the internet that can cause numerous problems for both users and companies. Blocking certain tools can make all the difference in combating cyber threats . Relying on the correct tool for your internet access control policy , such as Lumiun, helps the company reduce the chances of contamination by viruses and other malware that causes many damage.
Better Internet Performance
Since the internet is a resource that demands a lot from the equipment used in the business, blocking certain resources releases space and performance so that essential activities are performed with better quality. The better the internet used by the company, the better the competitive position of the business in the market and the better the quality of services and activities performed in the organization.
Monitoring on the use of the internet
Through an efficient lock tool, managers can more intelligently monitor the type of access that is done within the company, and from there, create more specific and intelligent access rules aimed at business quality .
Cost reduction with maintenance
As we said earlier, the internet is full of threats that can cause various damage to the company and users. Some of these threats may impair the proper functioning of machines, interrupting activities and making resources unavailable, generating maintenance costs. Avoiding improper access, the company does not create points of vulnerability and, consequently, does not suffer from cyber attacks.
How to create a more efficient access control policy with Lumiun?
From the tips we mentioned above, managers can establish a smarter process to create a quality internet access policy. It is very important that, in addition to the resources that are most commonly used by the company, those responsible know how is the user access profile.
With the help of Lumiun , it is possible to monitor the type of access that is performed and create more specific business rules . For example, if a certain group of employees often access more social networks, it is possible to block this access in a specific way.
If the most common access is made on sports sites and online games dissemination, policy can also be created based on this information. The important thing is for the company to block what really hinders activities and business continuity.
Lumiun has intelligent and efficient tools that will help managers establish an efficient and complete internet access control policy , all with easy use and intuitive panel. What are you waiting for to know our products and add even more productivity to your business?
Make a demonstration without commitment or request a free test.
Until later!