Understanding what phishing is very important to prevent you from being a cybercriminal victim, as phishing is a type of fraud performed electronically. This fraud aims to purchase personal data from the user, such as CPF, bank account numbers, passwords, ID, among other confidential data.
Before phishing also focused on stealing files such as music, documents and personal images, but it was modernizing and increasing its form of action, being increasingly dangerous attacks and can cause many problems for companies.
If you have an email account or social media profile, you are likely to have found a phishing of some kind before. In one sentence, phishing is the fraudulent attempt to steal personal information by social engineering: the act of criminal disappointment.
The first cases of phishing
These cases occurred over twenty years ago . In the early 1990s, attackers aimed at the once popular America online
It was not long before these threat actors identify higher value goals, pressuring innocent victims to “check their collection information” against the threat of excluding urgent accounts. Through this evolution, not only can criminal groups obtain the victims' AOL credentials, but also the bank account and payment card details.
AOL has intensified its anti -fraud operations, implementing new measures to proactively expel the accounts involved in Phishing. This was a decisive movement that led attackers to jump ships in search of new opportunities.
More than 400,000 phishing sites detected per month in 2016
According to the Webroot Phishing Threat Trends from December 2016, more than 400,000 phishing sites were detected per month last year.
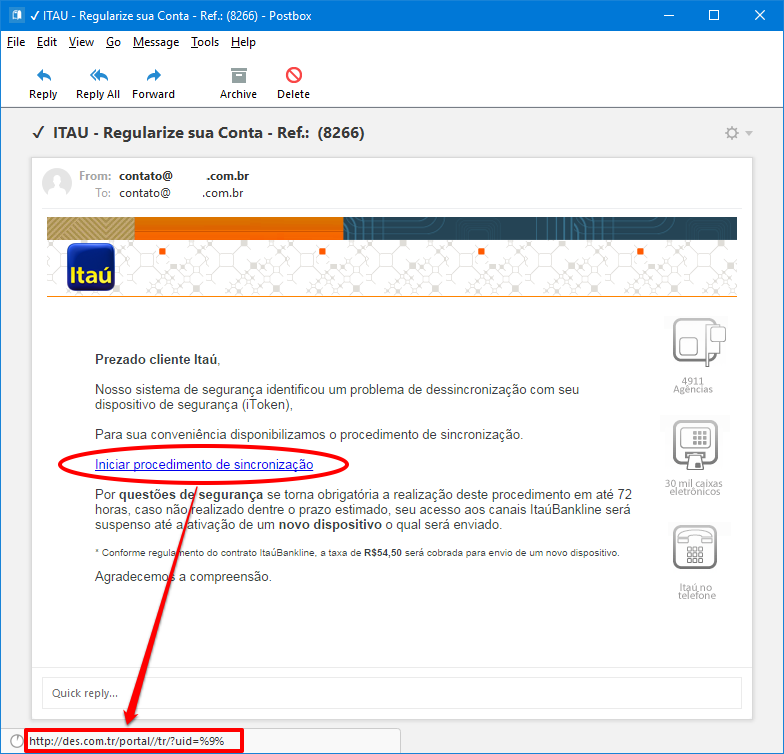
Phishing attacks use social engineering techniques to convince victims that they can trust what they are seeing and can provide important data. For example, a email requesting personal information for a lawsuit, or a fake page perfectly imitating a bank site and requesting passwords.
Phishing attacks have become increasingly sophisticated and developed to obtain sensitive information. Most attacks currently use tools that automate the creation of phishing sites, making them less than 24 hours - the average living time is 15 hours. This makes it more difficult for traditional security tools to block this kind of threat today.
Hal Lones, Webroot's CTO, stated that “years ago, these sites could last weeks or months, giving organizations enough time to block the attack method and prevent more victims from falling into the blow. Now phishing sites appear and disappear in the time of a coffee pause, leaving all organizations no matter how much serious and immediate risk of phishing attacks”.
Source: Webroot Quarterly Threat Update
How to remove and prevent phishing?
There is no way to remove phishing threats, they can definitely be detected. Have a way of monitoring your site and maintaining caution about what it should and should not be present there. If possible, change the main files of your site regularly.
To prevent phishing, some special care is needed, such as:
- Do not open attachments contained in email that were not requested earlier.
- Have good habits and do not respond to links added to unreserved emails.
- Protect your passwords and always use safe passwords.
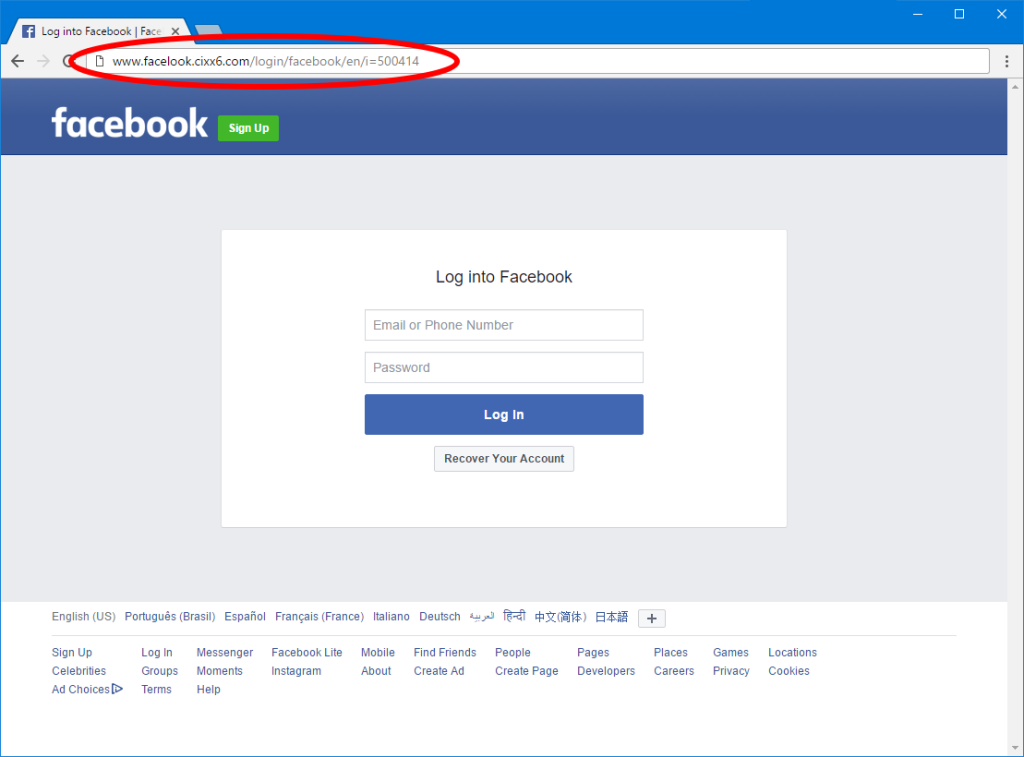
- Check the site URL. In many cases of phishing, the email address may seem legitimate, but the URL may be a spelling error or the domain may be different (.with when it should be .gov). This usually denounces the use of phishing.
- Keep your browser up to date and use security updates from your computer and system.












9 Comments
Comments closed